Secure Your Online Transactions: Essential Measures

Why Online Transaction Security Has Never Been More Critical
Online transaction security measures are the systems, processes, and technologies that protect digital payments from fraud, data breaches, and cyberattacks. With 71% of businesses reporting payment fraud attacks in 2021 and data breaches costing an average of $9.44 million in the US, securing your online transactions isn’t optional—it’s essential for survival.
Essential online transaction security measures include:
- Encryption (SSL/TLS) – Protects data during transmission
- Tokenization – Replaces sensitive card data with meaningless tokens
- Multi-Factor Authentication (MFA) – Adds extra verification layers
- PCI DSS Compliance – Industry-standard security requirements
- 3D Secure Authentication – Bank-verified customer identity checks
- Address Verification Service (AVS) – Matches billing addresses
- Real-time Fraud Monitoring – Detects suspicious transaction patterns
- Secure Payment Gateways – Process payments safely
The stakes couldn’t be higher. Research shows that 66% of US consumers won’t trust a brand after a data breach. Meanwhile, cyberattacks jumped 31% between 2020 and 2021, with 83% of organizations facing phishing attacks.
For online retailers processing millions in annual sales, a single security incident can destroy years of trust-building and tank your bottom line. The good news? Most security breaches are preventable with the right measures in place.
This guide will show you exactly how to implement bulletproof transaction security without breaking your budget or frustrating customers.
Why Online Transaction Security Matters
Remember when the biggest worry about online shopping was whether your package would arrive on time? Those days feel like ancient history now. The pandemic fundamentally transformed the digital payment landscape, creating a perfect storm of opportunity and risk.
By the end of 2020, nearly 80% of US shoppers were using some form of digital payment. While this opened incredible doors for businesses, it also painted a giant target on every online transaction.
The numbers tell a sobering story. Phishing attacks hit 83% of organizations in 2021—that’s up 26% from just the year before. Meanwhile, ransomware struck 59% of organizations, and payment fraud affected 71% of businesses.
But here’s what really keeps business owners up at night: data breaches now cost an average of $9.44 million per incident in the US. That’s enough to sink most businesses entirely.
The financial hit is just the beginning. When customers lose trust in your security, they don’t just complain—they disappear. Research shows 66% of US consumers won’t trust a brand after a cyberattack compromises their data.
For businesses handling customer data, GDPR compliance violations can result in fines up to €20 million or 4% of global turnover. Suddenly, online transaction security measures aren’t just about preventing fraud—they’re about keeping your doors open.
Key Risks Every Business Faces
Card-Not-Present fraud is the elephant in the room for online retailers. Without a physical card to verify, fraudsters use stolen card data to make purchases, leaving you with chargebacks.
Account takeover attacks use stolen credentials to slip into customer accounts undetected, then make unauthorized purchases or steal stored payment information. These attacks often fly under the radar for weeks.
Chargeback fraud—or “friendly fraud”—occurs when customers exploit the chargeback system by claiming legitimate purchases were unauthorized. They get their money back and keep the products while merchants eat the cost.
Electronic check abuse involves processing payments from accounts with insufficient funds, closed accounts, or completely fraudulent account information, resulting in significant preventable losses.
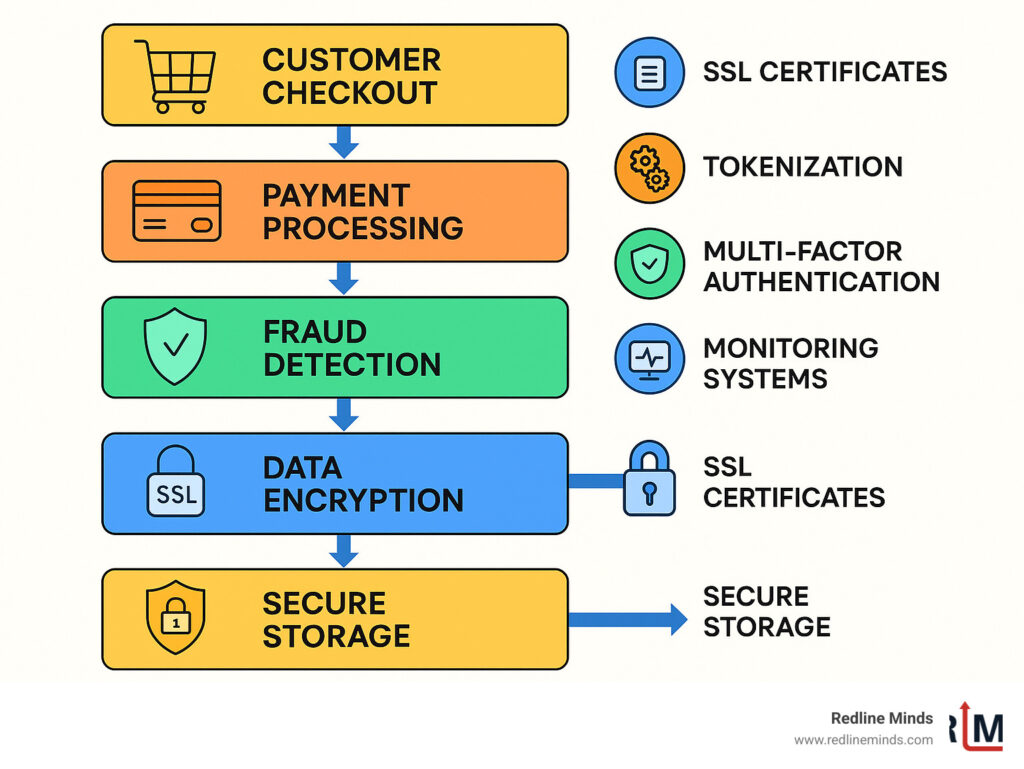
Top Online Transaction Security Measures
Building bulletproof online transaction security measures isn’t about finding one perfect solution—it’s about layering multiple defenses to create an impenetrable fortress around your customers’ data.
The beauty of a layered security approach is that even if one defense fails, others catch what slips through. Here’s how essential security technologies compare:
| Security Method | Protection Level | Implementation Cost | Customer Impact |
|---|---|---|---|
| SSL/TLS Encryption | High | Low | None |
| Tokenization | Very High | Medium | None |
| Multi-Factor Authentication | High | Low | Minimal |
| 3D Secure | Very High | Medium | Low |
| Address Verification | Medium | Low | None |
| Real-time Monitoring | High | High | None |
Encryption & Tokenization Essentials
SSL/TLS encryption is like having a secret code that only you and your customer know. When you see that little lock icon and “https://” in your browser, SSL/TLS is scrambling all data traveling between your customer’s device and your server.
Modern browsers mark HTTP sites as “not secure,” which can scare customers away. SSL certificates are often free through providers like Let’s Encrypt.
Encryption comes in two flavors: Data-in-transit encryption protects information while moving between systems, while data-at-rest encryption secures information in your databases and files.
Tokenization takes protection to the next level by replacing sensitive data with meaningless tokens. When customers enter card details, your payment processor immediately swaps that information for a unique token. Your system only sees the token—never the real card data.
Managing encryption properly is crucial for PCI DSS requirements. You’ll need to rotate encryption keys regularly, store keys separately from encrypted data, and consider hardware security modules for sensitive operations.
Multi-Factor Authentication Boosts Protection
Passwords alone provide false security. Multi-factor authentication (MFA) combines something you know (password) with something you have (phone) or something you are (fingerprint).
Options include SMS and email one-time passwords, authenticator apps like Google Authenticator, biometric authentication using fingerprints or face recognition, and hardware tokens for maximum security.
The smart approach is risk-based authentication—only triggering extra security when something looks suspicious, like logins from new devices or unusually large purchases. Device fingerprinting creates unique profiles based on technical details that are hard to fake.
Secure Payment Gateways & PCI DSS Compliance
Your payment gateway processes payments, stores sensitive data, and handles financial regulations. Look for Level 1 PCI DSS certification, end-to-end encryption, tokenization capabilities, built-in fraud detection, and 3D Secure support.
For different payment options, our guide to ecommerce payment options breaks down various solutions.
PCI DSS compliance requirements vary by transaction volume. The smartest strategy is scope reduction—limiting systems that touch cardholder data through hosted payment pages, tokenization, and point-to-point encryption.
Ongoing Monitoring, Patching & Incident Response

Real-time monitoring systems use machine learning to watch transaction patterns and flag suspicious activity. Security Information and Event Management (SIEM) systems collect information across your infrastructure, watching for unusual login patterns, failed authentication attempts, and suspicious transaction volumes.
Anomaly detection learns normal patterns for each customer and raises alerts when purchases deviate significantly. Patch management keeps software updated against known vulnerabilities—test patches safely, prioritize security updates, and maintain clear software inventories.
When incidents occur, having a solid incident response plan includes clear escalation procedures, communication templates, evidence preservation protocols, and recovery procedures.
Applying Online Transaction Security Measures to Specific Payment Types
Not all payments are created equal. Each payment method brings its own security challenges and opportunities. Let’s explore how to protect the most popular payment types your customers use.
Think of it like choosing the right lock for different doors in your house. Your front door needs a different security approach than your garden shed. The same principle applies to online transaction security measures—what works for credit cards might not be enough for mobile wallets or international transfers.
Electronic Checks & ACH
Electronic checks are a bit like the Wild West of online payments. Unlike credit cards, they don’t come with built-in fraud protection, which means prevention is your only real defense.
Here’s the challenge: when someone writes a bad e-check, you might not find out for days or even weeks. By then, the fraudster is long gone, and you’re stuck holding the bag.
Account verification should be your first line of defense. You can verify bank accounts through micro-deposits (sending tiny amounts that customers confirm) or real-time verification services that instantly check account validity.
NACHA compliance isn’t optional—it’s the law. The National Automated Clearing House Association sets strict rules for ACH transactions. Breaking these rules can result in hefty fines and losing your ability to process e-checks entirely.
Network segmentation keeps your e-check systems isolated from other parts of your infrastructure. If hackers break into one system, they can’t easily jump to others. It’s like having separate keys for different parts of your business.
Tokenization for e-checks works just like it does for credit cards. Instead of storing actual routing and account numbers, you store meaningless tokens. Even if someone steals your data, they get useless information.
Smart fraud filters can catch suspicious patterns before they become problems. Watch for things like multiple transactions from the same account in short periods, or accounts with histories of returns and chargebacks.
Mobile & Digital Wallets
Mobile payments are fascinating because they’re often more secure than traditional card payments, even though many people assume the opposite. Digital wallets like Apple Pay and Google Pay use security features that would make a bank jealous.
EMV tokenization replaces actual card numbers with unique tokens for every single transaction. Even if someone intercepts the payment data, they can’t use it again. It’s like getting a new credit card number for every purchase.
Device biometrics add a layer of security that’s incredibly hard to fake. Your fingerprint or face becomes your password, and unlike traditional passwords, you can’t forget it or write it down somewhere unsafe.
NFC encryption protects the communication between devices during contactless payments. The data is scrambled so thoroughly that intercepting it is practically useless.
PSD2 Strong Customer Authentication requirements in Europe are pushing mobile security even further. These regulations require two different types of authentication—something you know, something you have, or something you are. Most mobile wallets already exceed these requirements.
The beauty of mobile payments is that they often provide better security than traditional cards while being more convenient for customers. It’s a rare win-win situation.
International & Multi-Currency Transactions
Cross-border payments are like navigating a minefield blindfolded. You’re dealing with different currencies, regulations, and fraud patterns all at the same time.
Foreign exchange provider security becomes critical when you’re converting currencies. Make sure your FX provider uses the same security standards you’d expect from any financial institution. A weak link in the currency conversion chain can compromise your entire transaction.
Regulatory compliance gets complicated fast when you’re dealing with multiple countries. What’s perfectly legal in one country might violate regulations in another. The overlap between GDPR and CCPA creates particularly complex requirements if you serve both European and California customers.
Improved fraud screening is essential for international transactions because fraud patterns vary dramatically by region. What looks normal in one country might be a red flag in another. Your fraud detection systems need to understand these regional differences.
Secure remittance protocols become especially important for large cross-border transfers. These high-value transactions are attractive targets for cybercriminals, so they need extra protection.
If you’re processing payments from customers around the world, you need to meet the strictest applicable standards. It’s easier to build one robust system than to try managing different security levels for different regions.
The key is understanding that international payments aren’t just domestic payments with extra steps—they’re an entirely different security challenge that requires specialized approaches.
For more guidance on securing your specific payment setup, check out our SSL readiness information to ensure your foundation is solid before adding complex payment methods.
Building a Human Firewall & Managing Third-Party Risk

Even the most sophisticated online transaction security measures can fail if your team isn’t prepared. Your employees represent your first line of defense—and sometimes your biggest vulnerability.
You could have military-grade encryption and bulletproof payment gateways, but if someone clicks a phishing email or uses “password123” for their admin account, all those technical safeguards become useless.
After the pandemic began, only 40% of small businesses had adequate cybersecurity policies. Building a “human firewall” means creating a culture where security becomes second nature and the right processes make secure behavior the easy choice.
Employee & Customer Education
Regular phishing drills work effectively—employees who fall for simulated attacks become much more cautious afterward. Password hygiene training goes beyond strong passwords to include password managers and explaining why “Summer2024!” isn’t secure.
Least privilege access gives employees only the system access needed for their jobs. Customer service doesn’t need payment gateway admin access, and marketing doesn’t need database privileges.
Customer education builds trust and reduces fraud risk. When customers understand secure checkout pages and recognize legitimate communications, everyone wins. Trust badges and security certifications should be prominently displayed with plain English explanations.
Professional design matters for security perception. Customers associate clean, professional checkout pages with better security. Broken images, typos, or confusing layouts trigger security concerns.
Vendor & Platform Governance
Third-party vendors can introduce unseen security risks. Every app, payment processor, and hosting company represents a potential entry point for attackers.
Due diligence starts before contracts. Research vendors’ security track records, breach history, and certifications. Service level agreements (SLAs) should include specific security requirements and define breach response responsibilities.
Ongoing vendor monitoring catches problems early through Google alerts and regular security report reviews. Contractual controls should require 24-hour breach notifications, audit rights, and data deletion requirements.
For businesses handling ADA compliance, accessible payment forms must maintain security standards while remaining usable for customers with disabilities.
The goal isn’t eliminating all risk—it’s building human-centered security layers that complement technical measures. Well-trained teams understanding security become your strongest asset in protecting customer data.
Future Trends & Budget-Friendly Tips
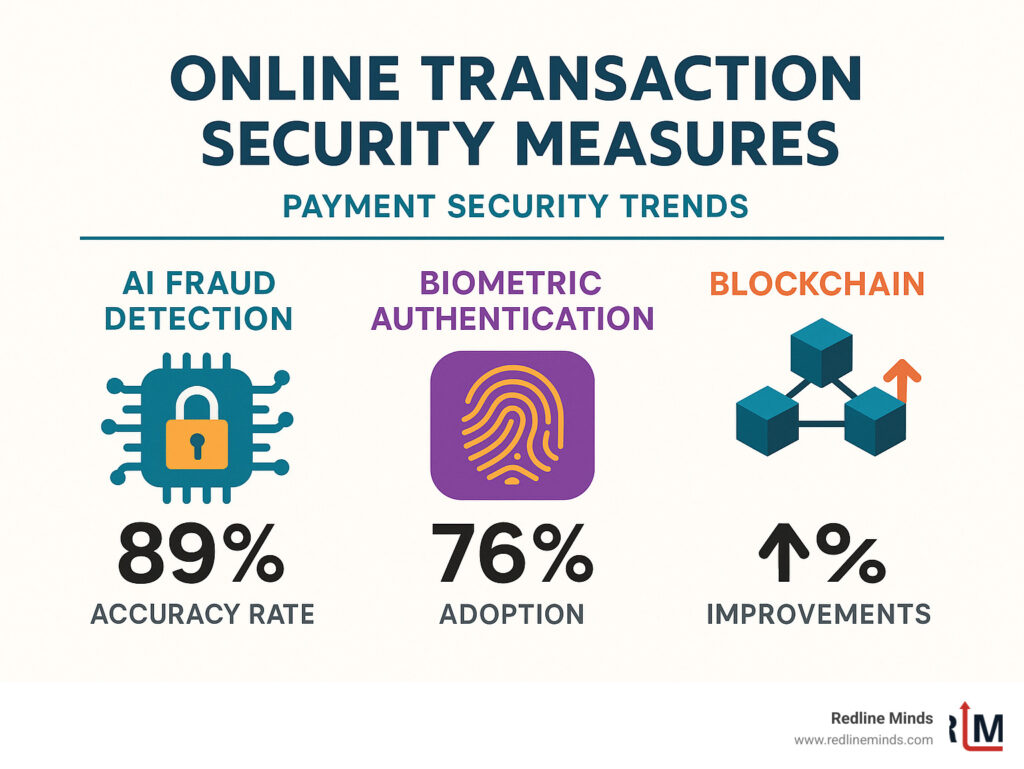
The payment security landscape is changing rapidly, and staying ahead is essential for survival. Artificial Intelligence and Machine Learning are revolutionizing fraud detection, learning from millions of transactions to spot patterns humans would miss.
Biometric authentication is moving beyond fingerprints to voice recognition, iris scanning, and behavioral biometrics. Blockchain technology creates unchangeable transaction ledgers, making fraud nearly impossible. Zero-trust architecture operates on “trust nothing, verify everything,” checking every user and device before granting access.
Open banking APIs create new opportunities for secure financial services through regulated interfaces that enable innovative payment solutions while maintaining strict security standards.
Low-Cost Wins for Small Merchants
You don’t need enterprise budgets to implement serious online transaction security measures. Free SSL certificates from Let’s Encrypt have democratized basic encryption—most hosting providers include these automatically.
Managed payment gateways handle PCI compliance heavy lifting, letting you leverage providers who’ve invested millions in protecting payment data. Cloud-based Web Application Firewalls protect against common attacks without requiring on-site hardware.
The SSL readiness requirements are now standard practice, often handled automatically by modern hosting platforms.
Basic cyber insurance has become affordable and comprehensive. Two-factor authentication apps like Google Authenticator cost nothing but add significant security. Hosted payment solutions reduce security burden by handling sensitive data off-site.
Research from Vercara shows that data breaches destroy e-commerce customer trust, with 75% of consumers abandoning brands after security incidents. But customers reward trusted businesses with loyalty and higher spending.
The future of payment security isn’t just preventing bad things—it’s building trust that drives long-term business success.
Frequently Asked Questions about Online Transaction Security Measures
Let’s address the most common questions we hear from ecommerce business owners about securing their online transactions. These answers will help you make informed decisions about protecting your customers and your business.
What is PCI DSS and who must comply?
PCI DSS stands for Payment Card Industry Data Security Standard, and if you accept credit cards online, it applies to you. Period. There’s no getting around it, whether you’re processing ten transactions a year or ten million.
The Payment Card Industry Security Standards Council created these requirements back in 2004. American Express, Visa, MasterCard, and Find all came together because they were tired of dealing with data breaches that could have been prevented.
Here’s what many business owners don’t realize: PCI compliance isn’t optional. Every merchant has a compliance level based on transaction volume, but everyone must follow the same 12 core security requirements. These cover everything from network security to employee access controls.
The good news? You don’t have to become a security expert overnight. Many payment processors and ecommerce platforms handle much of the compliance burden for you. The key is choosing partners who take security seriously and can help reduce your compliance scope.
How does tokenization differ from encryption?
This is probably the most confusing aspect of online transaction security measures for business owners. Both protect your customers’ payment data, but they work in completely different ways.
Think of encryption like a secret code. When someone enters their credit card number, it gets scrambled using complex mathematical formulas. The scrambled data can be unscrambled later using the right key. It’s like having a locked box where you need the right key to open it.
Tokenization works more like a coat check system. When a customer enters their card details, the system immediately swaps that information for a meaningless token—like getting a numbered ticket for your coat. The real card data gets stored securely in a separate “token vault,” and your system only keeps the worthless ticket.
Here’s why tokenization often wins for payment security: if hackers steal your tokens, they’re completely useless. There’s no mathematical relationship between the token and the original card number. Even with unlimited computing power, those tokens can’t be reverse-engineered back to real card data.
Many payment processors now offer tokenization as a standard feature, which is great news for merchants who want enterprise-level security without the complexity.
Which online payment method is safest for consumers?
Your customers probably ask you this question, and the answer might surprise them. Credit cards remain the gold standard for consumer protection in online transactions.
Federal law limits credit card fraud liability to just $50, and most major card issuers offer zero-liability policies. If someone steals your customer’s credit card information and goes on a shopping spree, the customer won’t pay a penny. Plus, credit card disputes don’t immediately drain bank accounts while investigations happen.
Digital wallets like Apple Pay and Google Pay are becoming even safer than traditional credit cards. They use tokenization (remember that coat check system?) plus biometric authentication. When someone pays with Apple Pay, they’re not sending their actual card number to you—they’re sending a one-time token that’s useless for future purchases.
Debit cards offer the least protection for consumers. Fraudulent debit transactions come directly out of bank accounts, and while customers can get their money back, it often takes days or weeks. During that time, they might face bounced check fees or other problems from insufficient funds.
As a merchant, understanding these differences helps you communicate security benefits to customers and choose payment options that build trust. When customers feel secure, they’re more likely to complete purchases and return for future business.
Conclusion
Building secure online transactions isn’t just about checking compliance boxes—it’s about creating a business foundation that customers can trust completely. When you implement comprehensive online transaction security measures, you’re building genuine customer confidence that translates directly into sales growth.
Every customer entering their credit card information makes an act of faith, trusting you with their financial security. When that trust is well-placed, customers return repeatedly. When broken, they disappear forever—and tell others about it.
Modern payment security’s beauty lies in its layered approach. Encryption protects data in transit, tokenization ensures stored information stays meaningless to hackers, multi-factor authentication adds verification without frustrating customers, and real-time fraud monitoring catches suspicious activity before problems occur.
Security isn’t a one-time project—it’s like tending a garden that needs regular attention. Threats evolve constantly, so your defenses must evolve too.
At Redline Minds, we’ve helped countless ecommerce businesses implement security measures that work in the real world. We understand that retailers need enterprise-level protection without enterprise-level complexity or costs.
We balance security with user experience because we’ve seen what happens when that balance goes wrong. Too little security makes you vulnerable to attacks that can destroy years of work. Too much friction causes customers to abandon carts before completing purchases.
Our ecommerce security and CRO services focus on creating secure checkout experiences that actually increase conversions. We help implement the right security measures for your specific situation.
The investment in proper security pays for itself through reduced fraud losses, improved customer retention, and better peace of mind. In today’s digital marketplace, customers expect bank-level security from every online retailer. Meeting those expectations isn’t optional—it’s the price of admission to successful ecommerce.
With the right security measures in place, you can honor customer trust while building a thriving online business that stands the test of time.